This is the multi-page printable view of this section. Click here to print.
Blog - NullPrivate Tech Sharing & Product Updates
- NingPing Ad-Block: DNS-Based Intelligent Ad-Filtering Solution
- Deep Dive: NullPrivate DNS Proxy – Bypass Restrictions and Safeguard Privacy
- Rebranding Announcement for AdGuardPrivate
- Added DDNS Support
- Better ECS Support
- NullPrivate - Enhanced DNS Service Based on AdGuard Home
- Full HTTP/3 Protocol Support
- Introducing Custom Client Names
- The Necessity of Ad Blocking: Safeguarding Attention and Privacy in the Digital Age
- Service Resource Optimization Strategy Guide
- Basic Memory Limit Adjustment
- Always Here to Support You
- How to Set Up a Dedicated Link
- All-new Upgrade – Enhanced Ad-blocking Rules
- Trial Service Details
NingPing Ad-Block: DNS-Based Intelligent Ad-Filtering Solution
In today’s digital era, advertising has become an integral part of the internet ecosystem, yet excessive ads not only degrade user experience but also pose privacy risks. NingPing (NullPrivate), a DNS service focused on privacy protection, adopts DNS-filtering technology similar to AdGuard Home to provide users with an effective ad-blocking solution.
How NingPing Ad-Block Works
NingPing’s ad-blocking relies on DNS (Domain Name System) filtering. The workflow is as follows:
flowchart TB
A[User Device] --> B{DNS Query}
B --> C[NingPing DNS Server]
C --> D[Query Domain Database]
D --> E{Ad or Tracker Domain?}
E -->|Yes| F[Return Null or Loopback]
E -->|No| G[Return Correct IP]
F --> H[Block Ad Load]
G --> I[Normal Site Access]DNS Request Monitoring
When your device tries to visit a website, it first queries the DNS server for the domain’s IP address. Acting as your primary DNS server, NingPing receives and analyzes these queries.
Intelligent Filtering
NingPing maintains a large database of advertising and tracking domains. When it detects a request for such a domain, the system blocks it immediately.
Efficient Response
For blocked requests, NingPing returns a null address or the local loopback address (e.g., 127.0.0.1), preventing ad content from loading. For legitimate requests, NingPing supplies the correct IP so users can access the intended site normally.
Technical Advantages
Efficiency
- Network-level blocking: Ads are stopped at the DNS-resolution stage, before any web content is downloaded.
- Millisecond-level response: Localized DNS responses add virtually no latency.
- Whole-network protection: One configuration shields every device on the network.
Precision
- Multi-layer filtering: Supports exact domain matching, wildcard rules, and regular expressions.
- Smart categorization: Rules are grouped by ads, trackers, malware, etc.
- Dynamic updates: Regularly pulls the latest rules from trusted sources.
Privacy Protection
- No-trace browsing: No user-visit logs are kept.
- Reduced data leakage: Prevents advertisers and trackers from harvesting user data.
- Local processing: Most filtering occurs locally, minimizing data exposure.
Similarities to AdGuard Home
NingPing and AdGuard Home share the same core ad-blocking principles:
- DNS-based filtering: Both intercept DNS queries to block ad domains.
- Rule management: Both allow custom rules and whitelist/blacklist configuration.
- Network-wide protection: Both can safeguard an entire LAN.
- Open-source community: Both benefit from community-maintained filter lists.
User-Experience Optimizations
NingPing is designed to block ads effectively without disrupting normal use.
Transparent Management
- Detailed blocking statistics let users see protection effectiveness.
- Flexible whitelist settings prevent accidental blocking of important sites.
- Rule updates take effect instantly—no device restart required.
Ease of Use
- Simplified setup process—accessible even for non-technical users.
- Multi-language support for global audiences.
- Compatible with all network environments and device types.
- Secure, reliable DNS infrastructure.
Privacy Safeguards
- Strict privacy measures protect user data.
- No personally identifiable information is collected.
- User data remains secure.
Usage Recommendations
For optimal ad-blocking:
- Configure rules wisely: Choose filter lists that match your needs.
- Check for updates regularly: Keep rule databases current.
- Review statistics: Use stats to gauge blocking effectiveness.
- Adjust whitelists promptly: Add mistakenly blocked sites to the whitelist.
Conclusion
Using advanced DNS filtering, NingPing delivers an efficient, precise, and privacy-centric ad-blocking solution. We protect users from intrusive ads while preserving normal web experiences. Choose NingPing for a cleaner, safer internet.
In the digital age, everyone deserves a private, uncluttered online space. NingPing is built to deliver exactly that, helping users reclaim control of their digital lives.
Deep Dive: NullPrivate DNS Proxy – Bypass Restrictions and Safeguard Privacy
🌐 DNS Proxy Deep Dive
In today’s complex network landscape, traditional DNS services often hit numerous roadblocks. NullPrivate DNS now fully supports upstream DNS proxying, giving users a more flexible and secure browsing experience.
Why You Need DNS Proxying
In some environments—corporate networks, campus networks, or region-specific setups—direct access to upstream DNS servers can face these issues:
- Network Restrictions: DNS servers like 1.1.1.1 or 8.8.8.8 may be blocked by firewalls
- ISP Interference: Carriers can redirect or poison DNS queries
- Geo-blocking: DNS services in certain regions may be inaccessible
- Privacy Concerns: You may need to hide your real IP behind a proxy
🚀 Core Features
DoH & DoT Proxy Support
Built on AdGuard Home and heavily customized, NullPrivate DNS adds these key capabilities:
Smart DNS Split-Horizon
- Auto-detects network conditions
- Intelligently chooses direct vs. proxy routes based on rules
- Supports custom split-horizon config files
Full Proxy-Protocol Coverage
- HTTP proxy (
http_proxy) - HTTPS proxy (
https_proxy) - SOCKS5 proxy (
socks5)
- HTTP proxy (
Secure Encrypted Transport
- DoH (DNS over HTTPS) proxy support
- DoT (DNS over TLS) proxy support
- End-to-end encryption for privacy
📋 Step-by-Step Configuration
Environment Variables
Enabling DNS proxying is as simple as setting the right proxy variables in your environment.
Linux / macOS
# Temporary (current shell)
export http_proxy="http://proxy.example.com:8080"
export https_proxy="http://proxy.example.com:8080"
export ALL_PROXY="socks5://[username:password@]proxyhost:port"
# Permanent (add to ~/.bashrc or ~/.zshrc)
echo 'export http_proxy="http://proxy.example.com:8080"' >> ~/.bashrc
echo 'export https_proxy="http://proxy.example.com:8080"' >> ~/.bashrc
echo 'export ALL_PROXY="socks5://[username:password@]proxyhost:port"' >> ~/.bashrc
source ~/.bashrc
Windows
# Command Prompt
set http_proxy=http://proxy.example.com:8080
set https_proxy=http://proxy.example.com:8080
# PowerShell
$env:http_proxy="http://proxy.example.com:8080"
$env:https_proxy="http://proxy.example.com:8080"
Docker Container
version: '3.8'
services:
nullprivate-dns:
image: nullprivate/nullprivate:latest
environment:
- http_proxy=http://proxy.example.com:8080
- https_proxy=http://proxy.example.com:8080
ports:
- "53:53/tcp"
- "53:53/udp"
- "80:80/tcp"
- "443:443/tcp"
Advanced Options
Authenticated Proxy
If your proxy requires credentials, use this format:
export http_proxy="http://username:password@proxy.example.com:8080"
export https_proxy="https://username:password@proxy.example.com:8080"
Exclude Specific Domains
Skip the proxy for certain domains via the no_proxy variable:
export no_proxy="localhost,127.0.0.1,.local"
🔧 Real-World Use Cases
Corporate Networks
In enterprise environments where external DNS is firewalled, proxying lets you:
- Bypass corporate firewall restrictions
- Reach blocked DNS services
- Securely access external networks
Campus Networks
Campus networks often impose strict DNS controls; proxying helps you:
- Avoid DNS hijacking or pollution
- Achieve faster resolution times
- Protect student privacy and study data
Home Network Protection
Home users can:
- Conceal the real home IP
- Prevent ISP tracking of browsing habits
- Provide safer internet for children
⚡ Technical Advantages
| Feature | AdGuard Home | Traditional DNS | NullPrivate DNS Proxy |
|---|---|---|---|
| DoH Proxy Support | ❌ | ❌ | ✅ |
| DoT Proxy Support | ❌ | ❌ | ✅ |
| Smart Split-Horizon | ❌ | ❌ | ✅ |
| Config Complexity | Medium | Simple | Simple |
| Network Adaptivity | Average | Average | Excellent |
| Privacy Protection | Good | Average | Excellent |
🛠️ Troubleshooting Guide
Common Issues & Fixes
Q: DNS resolution fails after enabling proxy
Likely causes:
- Proxy unreachable
- Proxy lacks HTTPS support
- Connectivity issues
Solutions:
- Test proxy:
curl -x http://proxy.example.com:8080 https://www.google.com - Verify env vars:
env | grep proxy - Restart NullPrivate service
Q: Proxy connection timeouts
Likely causes:
- Slow proxy response
- High latency
- Overloaded proxy
Solutions:
- Switch proxy server
- Adjust DNS timeout settings
- Load-balance across multiple proxies
Q: Specific domains resolve incorrectly
Likely causes:
- Domain on proxy blacklist
- DNS cache issues
- Misconfigured proxy DNS
Solutions:
- Flush DNS cache
- Review proxy config
- Try direct mode
📊 Performance Monitoring
After proxying is enabled, monitor:
- DNS query latency – see if resolution speeds improve
- Success-rate stats – track proxy connection success
- Traffic analysis – review proxy bandwidth usage
- Error logs – scan system logs regularly for issues
🔒 Security Best Practices
- Use trusted proxies – rely on reputable providers
- Prefer encryption – choose HTTPS proxies when possible
- Rotate proxies – periodically change servers for added safety
- Monitor traffic – keep an eye on proxy usage
- Update configs – refresh settings as networks evolve
🎯 Wrap-up & Roadmap
NullPrivate DNS proxy delivers a flexible, secure way to use DNS in restrictive environments. With minimal configuration, you can bypass limitations and enjoy better privacy.
Coming Next
- SOCKS5 proxy protocol support
- Smart proxy-selection algorithms
- Graphical configuration UI
- Multi-proxy load balancing
🚀 Try It Now
Ready to experience NullPrivate DNS proxy?
- Visit the GitHub repo
- Follow the deployment docs
- Set your proxy environment variables
- Enjoy a safer, freer internet
Rebranding Announcement for AdGuardPrivate
We recently received a notice from AdGuard stating that “AdGuard” is a registered trademark and may not be used without authorization, even with prefixes or suffixes, as such usage could constitute infringement. To avoid legal risks, our service has been officially renamed “NullPrivate”.
For existing users, your service remains completely unaffected. We will continue to serve you via the adguardprivate.com domain; only the official website and contact information will be migrated.
To prevent new users from mistakenly associating NullPrivate with AdGuard, we hereby clarify: our software product is forked from AdGuardHome and enhanced with new features. All code is open-source and adheres to the same GPLv3 license.
Repository: https://github.com/nullprivate/nullprivate
Users are welcome to review the code and deploy it themselves. Meanwhile, our SaaS version will continue to offer more affordable pricing and more stable service.
Thank you for your ongoing support—may our service keep bringing you value!
Added DDNS Support
If you already run a NullPrivate service, you can now enable the built-in DDNS feature.
Overview
NullPrivate has open-sourced its DDNS scripts. This Dynamic DNS (DDNS) is designed to give you an easy, no-cost way to set up a private Dynamic DNS without purchasing a domain. These scripts are built specifically for nullprivate.com and plug right into the core NullPrivate workflow.
Getting Started

- Make sure NullPrivate is deployed and running.
- Head to DNS Rewrite and download the DDNS script.
- Run the script.
Windows
Set-ExecutionPolicy Bypass -Scope Process
./ddns-script.ps1
Linux/macOS
chmod +x ddns-script.sh
./ddns-script.sh
Features
- Fast, simple setup—configure in just a few steps.
- Built on NullPrivate—DDNS is powered by NullPrivate’s core functionality.
- Cross-platform—works on Windows and Unix-like systems.
- Multiple auth options—use a cookie (more secure but expirable) or username/password (long-lived but less secure).
Differences from Traditional DDNS
When compared with traditional services, this private DDNS has the following advantages:
- No TTL—changes take effect instantly, no waiting for DNS caches to expire.
- Zero propagation delay—updates are immediately available everywhere the private DNS is used.
- No domain purchase required—use pseudo-domains for access; no paid domain needed.
- Privacy first—only users connected to your private DNS can resolve the records.
Quick-Start Guide
- Ensure NullPrivate is deployed and running.
- Follow the inline instructions in
win/ddns.ps1(Windows) orunix/ddns.sh(Unix-like systems) to configure your private DDNS.
Repository: https://github.com/NullPrivate/nullprivate-ddns
Better ECS Support
To provide the best DNS resolution experience, we have preset some recommended configurations, but there is still one setting that requires your attention: “EDNS Client Subnet”.
Enable EDNS Client Subnet (ECS)
For an even better experience, you may want the DNS server to return the server IP closest to your geographic location. EDNS Client Subnet (ECS) makes this possible. It allows sending a subnet containing geolocation information to the DNS server so that the server can return the optimal DNS resolution result.
How it works:
When ECS is enabled, your DNS resolver (e.g., AdGuard Home) includes a portion of the client IP address (usually the first 24 bits, representing the subnet where the client is located) in the DNS query and sends it to the upstream DNS server. The upstream DNS server then returns the server IP address most suitable for that region based on this subnet information.
sequenceDiagram
participant Client
participant DNS Resolver
participant Upstream DNS Server
Client->>DNS Resolver: DNS Query
DNS Resolver->>Upstream DNS Server: DNS Query with ECS (Client Subnet)
Upstream DNS Server->>DNS Resolver: DNS Response (Geo-localized IP)
DNS Resolver->>Client: DNS Response (Geo-localized IP)Privacy considerations:
Enabling ECS can improve DNS resolution accuracy and speed, but it may also have privacy implications. By sharing the subnet of your client IP address, your approximate geographic location may be recorded by the upstream DNS server. Please weigh whether to enable this feature based on your own circumstances.
How to weigh:
Enabling ECS can balance access speed and accuracy. If you have high privacy requirements, you can choose to disable ECS, but this may reduce access speed. If you want the best access experience, you can enable ECS, but please be aware of the potential privacy impact. This privacy information is collected by the upstream DNS; this service still adheres to the privacy policy commitment of not collecting or utilizing any information.
NullPrivate - Enhanced DNS Service Based on AdGuard Home
NullPrivate: Privacy-First DNS Service
Visit the official site to learn more: NullPrivate
This project is a secondary development based on AdGuard Home and follows the GPL 3.0 open-source license.
Source code is open at: GitHub - NullPrivate/NullPrivate
Enhanced Features
Compared to the original AdGuard Home, we have added the following capabilities:
- 📜 Automated SSL Certificate Management
- Automatic certificate issuance and renewal
- Support for wildcard certificate configuration
- 🛡️ Enhanced Security Features
- Intelligent rate-limiting protection
- Optimized access experience for mainland China
- ⚙️ Optimized System Configuration
- DHCP service disabled to focus on DNS functionality
- 🔄 DDNS Support
- 🌉 Proxy Support
- Download configuration files via proxy
- DoH/DoT proxy support
- 🚦 DNS Split-Horizon Support
- 🚫 Anti-addiction App List Support
Managed Service Advantages
We provide a professional DNS hosting service with the following characteristics:
- 🏢 Deployed on Alibaba Cloud Hangzhou nodes
- 🌐 Comprehensive protocol support
- IPv6 support, directly connected to mainstream IPv6 upstreams
- DoT (DNS over TLS)
- DoH (DNS over HTTPS)
- HTTP/3 support, significantly reducing latency
- 📊 Powerful rule management
- Support for importing third-party allow/deny lists
- Capacity for 1 million rules
- 📝 Comprehensive logging and statistics
- 72-hour query log retention
- 24-hour detailed statistical analysis
- ⚖️ Load balancing
- Multi-server distributed deployment
- Intelligent load distribution
- 💰 Competitive pricing
Performance & Effectiveness Evaluation
Ad blocking at the DNS layer has unique advantages:
💪 Strengths
- Zero additional power consumption
- Coverage across all devices
- Reduced device network wake-up frequency
- Fewer invalid data loads
⚠️ Limitations
- Lower blocking accuracy compared to browser extensions
- Cannot achieve the filtering effect of MITM solutions
Especially suitable for mobile device usage scenarios, balancing privacy protection with battery life.
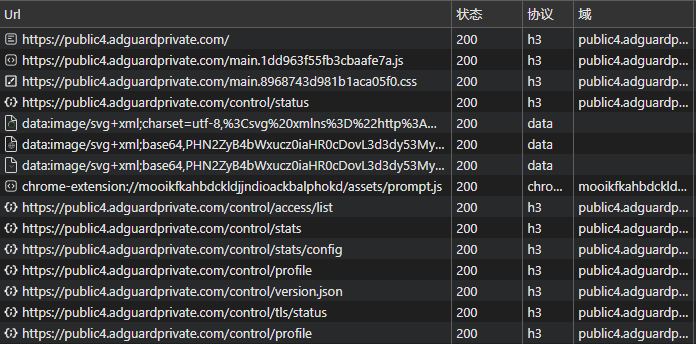
Full HTTP/3 Protocol Support
NullPrivate now fully supports the HTTP/3 protocol. All existing users will be automatically upgraded to enjoy the performance gains of HTTP/3 without any additional configuration.
Key Update Notes
- iOS users: Can now use HTTP/3 directly via the DoH protocol, enjoying lower network latency
- Android users: Due to system limitations, still use the DoT protocol for now; support will arrive once Google releases a subsequent version
- Performance boost: First-response times are significantly faster compared to HTTP/2, and connections are established more quickly
- Smart fallback: In environments that do not support HTTP/3, the system automatically falls back to HTTP/2 to ensure service stability
Deep Dive into HTTP/3 Technology
HTTP/3, the latest version of the HTTP protocol, is built on Google’s QUIC transport protocol and brings several revolutionary technical advantages:
Core Features
QUIC protocol over UDP
- Dramatically reduces connection-establishment time
- Improved multiplexing capabilities
- Smarter packet-loss handling
Optimized performance
- Zero-round-trip-time (0-RTT) handshakes
- Enhanced congestion control
- Connection-migration support
Enhanced security
- Integrated TLS 1.3
- Encrypted handshake process
- Reduced risk of man-in-the-middle attacks
Connection-Establishment Comparison
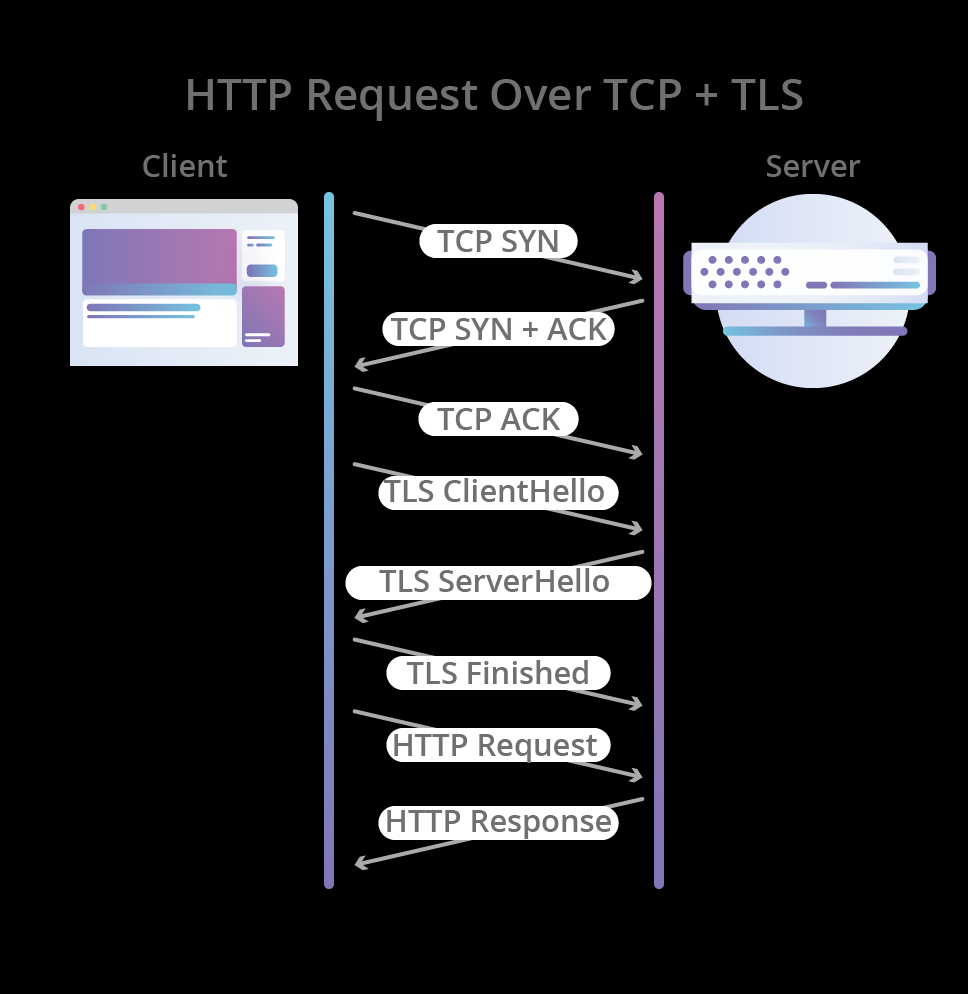
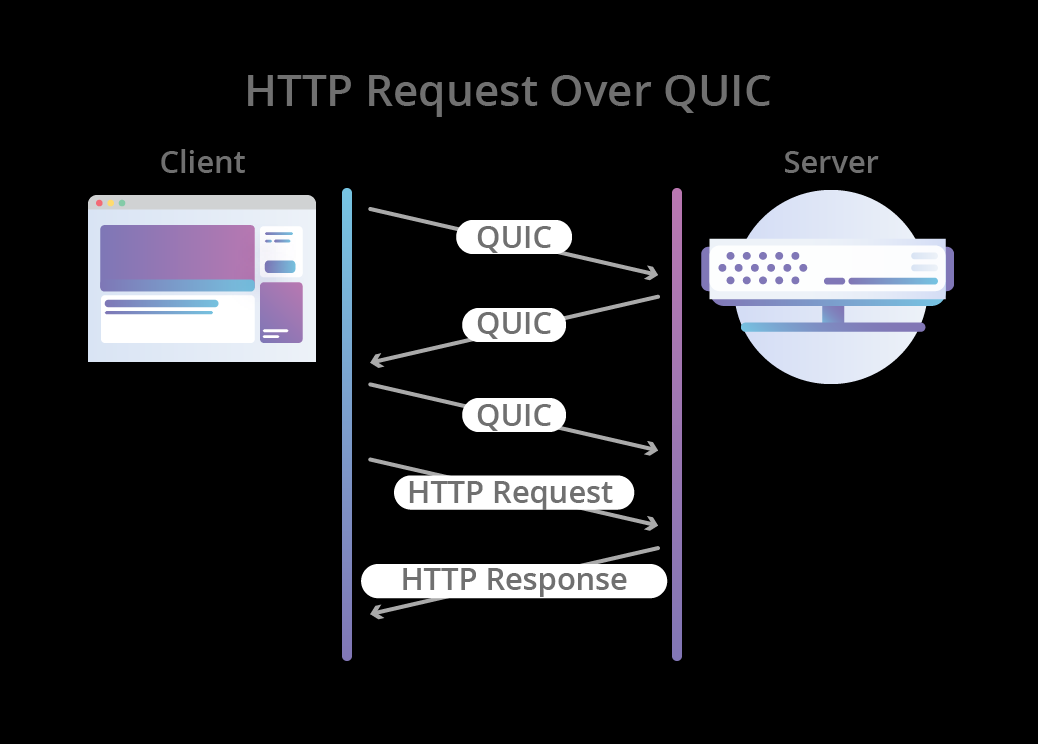
Usage Recommendations
- Ensure your client supports the HTTP/3 protocol
- Keep your client up to date
- When network conditions are restricted, the system will automatically fall back to HTTP/2
Important Notes
- In some regions, networks may restrict UDP traffic, affecting HTTP/3 performance
- Performance may vary across different network environments
- The system will automatically select the optimal protocol based on network conditions
References
Introducing Custom Client Names
Feature Overview
To enhance the user experience, NullPrivate now supports custom client names. With this feature, you can assign a unique label to each device, making device management more intuitive and convenient.
Configuration Guide
Setup varies slightly by device type:
Android
Simply prepend your custom prefix to the domain:
{device-name}.{original-domain}
Example: xiaomi-15pro.xxxxxxxx.nullprivate.com
iOS
- Open the “Setup Guide” page
- Enter your custom name in the “Client ID” field
- Download and install the new profile
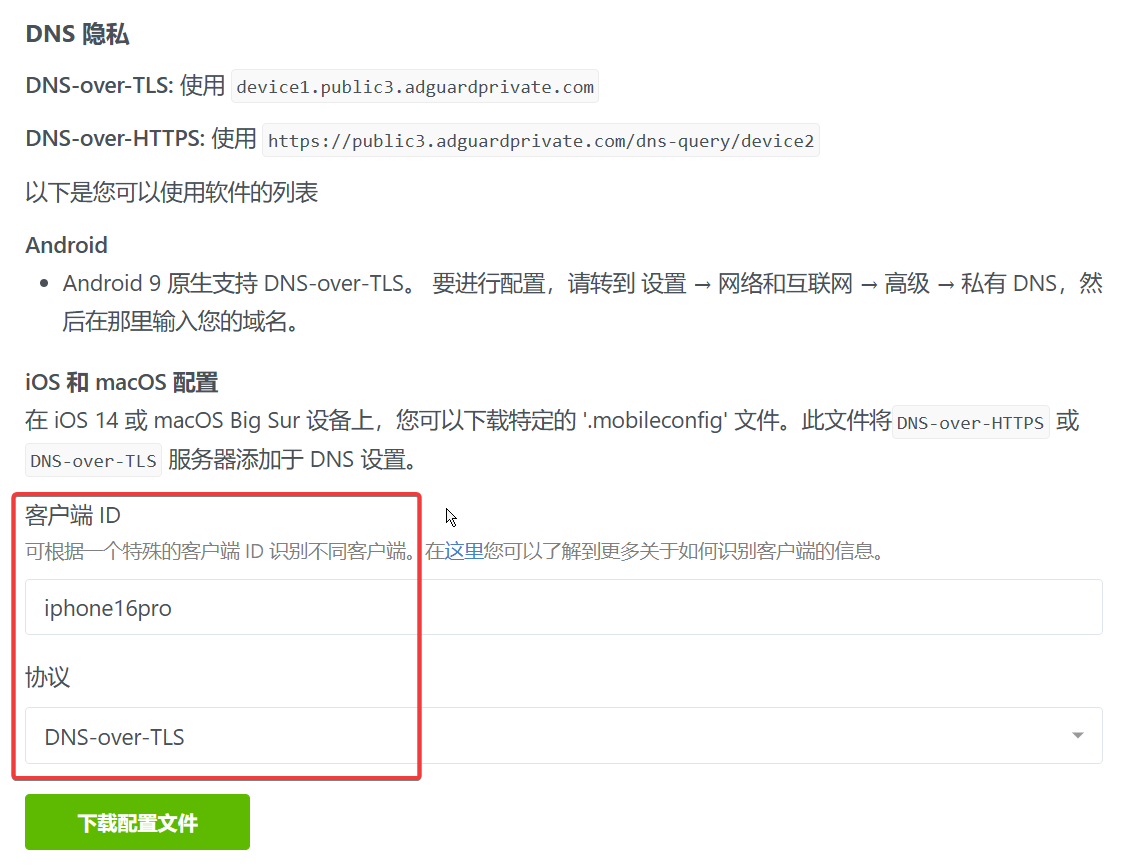
Browser (DoH)
Add the custom identifier after the existing DoH address:
Original:
https://xxxxxxxx.nullprivate.com/dns-query
New:
https://xxxxxxxx.nullprivate.com/dns-query/{device-id}
Example: https://xxxxxxxx.nullprivate.com/dns-query/pc1-browser
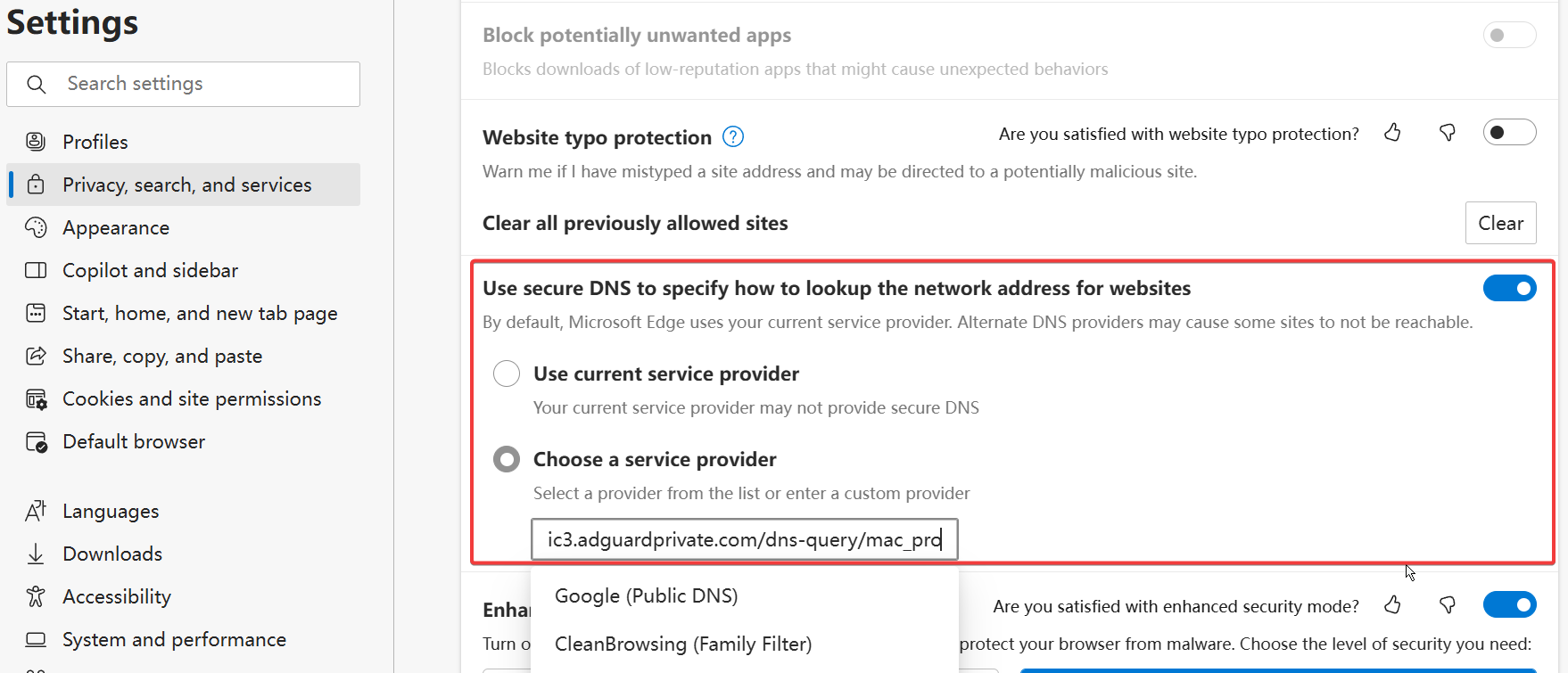
Usage Tips
- Use meaningful labels such as device model, location, or purpose.
- Stick to letters, numbers, and hyphens; avoid special characters.
- Maintain a consistent naming convention to simplify future management.
Important Notes
- Custom names only affect the display and do not impact service performance.
- You must re-apply the configuration after changing a name.
- Save each device’s configuration for easy reference later.
The Necessity of Ad Blocking: Safeguarding Attention and Privacy in the Digital Age
Deconstructing the Modern Advertising Ecosystem
The Advertiser Profit Model
The contemporary advertising system rests on a complex chain of interests:
- Advertisers connect marketers and users through media platforms
- Revenue comes from marketers’ placement fees, not from users
- The goal is to maximize “conversion rates”—turning ad viewers into paying customers
The Battle for Conversion
In this war for attention:
- Higher conversion rates translate into higher ad prices
- Ad-delivery efficiency directly affects revenue
- “Personalized targeting” has become the core strategy for boosting conversions
The Truth Behind Personalized Ads
The Depth of Data Collection
Modern ad systems harvest user information through multiple channels:
- Device identifiers and operating-system data
- Cross-platform behavioral tracking
- Social-relationship network analysis
- Consumer-habit profiling
The Trap of Precise Targeting
Seemingly convenient personalized feeds hide real risks:
- Exploiting cognitive biases to manufacture demand
- Amplifying latent user anxieties
- Creating false urgency
How Advertising Erodes Attention
The Cost of the Attention Economy
- Frequent interruptions undermine productivity
- Distorts decision-making ability
- Increases cognitive load
- Blurs the boundary of genuine needs
The Evolution of Ad Strategies
Modern advertising has moved beyond simple information delivery to:
- Forced memory implantation
- Emotional stimulation
- Anxiety marketing
- Social pressure
Strategies for Self-Protection
Core Protective Measures
Privacy First
- Restrict app permissions
- Control data sharing
- Use privacy-protection tools
Attention Management
- Set focused time blocks
- Build information-filtering mechanisms
- Cultivate the habit of actively seeking information
Consumption Decision Control
- Establish a needs-assessment system
- Delay purchase decisions
- Maintain rational judgment
Technical Support: Cyber Savvy
In this data-driven era, maintaining “cyber savvy”—caution and wisdom in the digital realm—is vital. This includes:
- Managing digital footprints
- Protecting personal privacy
- Controlling information flow
Solutions
“NingPing” is a comprehensive protection suite that goes beyond ad blocking to help users:
- Safeguard personal privacy
- Optimize browsing experiences
- Reduce attention fragmentation
- Provide a controllable information environment
Let’s reclaim our digital lives—starting by rejecting intrusive ads.
Service Resource Optimization Strategy Guide
Background
As user numbers grow and feature demands increase, we have observed that certain high-resource-consumption configuration options can lead to service instability. To ensure service quality, we conducted an in-depth analysis and formulated a corresponding optimization plan.
Resource Optimization Strategy
1. Filter Update Mechanism Optimization
Current Situation
- Some users have configured hourly filter updates
- Each update requires a full download-parse-deduplication cycle
- International bandwidth limitations prolong update times
- Server resources remain under continuous high load
Optimization Plan
We have adjusted the minimum update interval to 72 hours for the following reasons:
- Most filter lists update on a 24–72 hour cycle
- Reduces ineffective resource consumption
- Ensures service stability
- Improves bandwidth utilization efficiency
Impact Assessment
- Positive impacts
- More stable service response
- More reasonable resource usage
- Reduced system load
- Minimal impact
- Rule updates still occur within a reasonable cycle
- No effect on protection efficacy
2. Parallel Request Strategy
Current Situation
Most users currently have parallel requests enabled, but under the existing architecture the benefits are limited:
- Latency differences among Alibaba Cloud upstream services are typically within 5 ms
- May trigger Alibaba Cloud public service request-rate limits
- Adds unnecessary system overhead
Usage Recommendations
- We recommend using load-balancing mode
- Parallel requests are suitable for:
- Scenarios with significant upstream latency differences (>200 ms)
- Cases of unstable service quality
- Cross-border access scenarios
Note: We have not yet observed any throttling issues caused by parallel requests, so this feature remains available for now.
3. Third-Party List Management
Security Considerations
To ensure system stability, we have temporarily disabled support for certain third-party lists:
- External list sizes are unpredictable
- May lead to resource overruns
- Service stability cannot be guaranteed
Future Plans
We are researching a safer third-party list management solution so that this feature can be re-enabled in the future.
Basic Memory Limit Adjustment
Some users’ environments restart frequently; checking the logs shows the exit reason is memory usage hitting the 300 MB limit, causing a forced shutdown.
We are now raising the per-container limit to 500 MB to alleviate the restart issue.
If your environment experiences login or restart problems, please don’t hesitate to contact us at any time—solving customer issues is our responsibility.
Need help?
Contact on WeChat
private6688
or
Send email
service1@nullprivate.com
Please describe your issue in detail, and we will respond as soon as possible.
Always Here to Support You
Quick Start Guide
To help you get up and running with our service as smoothly as possible, we’ve prepared a detailed User Guide.
Thoughtful Support Service
Personalized Guidance
We understand that new users may face challenges when first getting started. Therefore, we:
- Continuously refine the structure of our product documentation
- Provide clear configuration guides
- Have prepared an extensive FAQ
Timely Response
While we employ a registration-free system to protect user privacy, that does not compromise the support we provide. You can reach us through the following channels:
Need help?
Contact on WeChat
private6688
or
Send email
service1@nullprivate.com
Please describe your issue in detail, and we will respond as soon as possible.
How to Set Up a Dedicated Link
Some paid AdGuard Home services provide a dedicated link but do not allow users to access the admin panel; the provider manages the rules on their behalf.
This indicates that they do not offer a private admin backend; the service is simply delivered through a domain-based reverse proxy, keeping costs relatively low.
You need to rent a server to run AdGuard Home and configure an Nginx reverse proxy to achieve this functionality.
Taking the service link 5r69hxdx9onl70hp.example.com as an example, the key Nginx configuration is as follows:
http {
server {
listen 1080;
server_name 5r69hxdx9onl70hp.example.com;
location / {
proxy_pass http://worker.example.com:5002;
proxy_set_header Host $http_host;
}
}
server {
listen 1443 ssl;
server_name 5r69hxdx9onl70hp.example.com;
ssl_certificate /app/data/certs/5r69hxdx9onl70hp/fullchain.pem;
ssl_certificate_key /app/data/certs/5r69hxdx9onl70hp/privkey.pem;
location / {
proxy_pass https://worker.example.com:5003;
proxy_set_header Host $http_host;
}
}
}
stream {
ssl_protocols TLSv1.2 TLSv1.3 SSLv3;
map $ssl_preread_server_name $targetBackend {
5r69hxdx9onl70hp.example.com worker.internal.com:5004;
}
server {
listen 1853;
proxy_pass $targetBackend;
ssl_preread on;
}
}
For each paying user you only need to add one similar Nginx block and point the domain’s DNS to the server. When the number of users grows and load on a single application instance becomes high, you can proxy to different back ends.
Such services cannot achieve true personalization; users must be able to enter the admin panel to truly control their own browsing data. This is the advantage of our private service—each user truly has an exclusive instance and can use all NullPrivate features.
All-new Upgrade – Enhanced Ad-blocking Rules
Rule Update Notes
To meet users’ demand for more robust ad blocking, we’ve completely overhauled our filtering rule strategy. The new version significantly improves ad-filtering effectiveness while keeping false-positives low. This update stems from user feedback; on the premise of ensuring normal website access, we have added more precise interception rules.
Rule List Overview
We have compiled the following professional rule lists; you can choose the ones that fit your needs:
Basic Protection Rules
| Category | AdGuard | Description |
|---|---|---|
| Ad Blocking | Link | Comprehensive filtering of all ad servers and ad sites |
| Tracking Protection | Link | Stops user-behavior tracking and personal-data collection |
| Redirect Protection | Link | Prevents malicious URL redirects |
Content Filtering Rules
| Category | AdGuard | Description |
|---|---|---|
| Fraud Sites | Link | Websites designed to deceive users |
| Ads | Link | Ad servers and advertising websites |
| Cryptocurrency | Link | Cryptocurrency and mining-related sites May affect legitimate crypto sites |
| Drugs | Link | Illegal drug sites Includes prescriptions illegal to possess in the US |
| Everything | Link | All domains from non-test lists combined |
| Link | Blocks FB and associated services | |
| Fraud | Link | Fraudulent sites |
| Gambling | Link | All gambling sites—legal and illegal |
| Malware | Link | Known malware-hosting sites |
| Phishing | Link | Sites used for phishing |
| Piracy | Link | Known illegal download sites |
| Porn | Link | Pornographic or porn-promoting sites |
| Ransomware | Link | Known ransomware hosts or sites containing ransomware |
| Redirect | Link | Sites that redirect you from where you expected to go |
| Scam | Link | Sites aimed at scamming users |
| TikTok | Link | Blocks TikTok and related services |
| Torrent | Link | Torrent indexes May block legitimate trackers distributing open-source software |
| Tracking | Link | Sites dedicated to tracking and gathering visitor information |
Usage Recommendations
Step-by-Step Adoption
- Start with the basic protection rules
- Gradually add other rules as required
- Review and update lists periodically
Performance Optimization
- Avoid enabling too many rules at once
- Prioritize the rules most relevant to your needs
- Clean up unused rules on a regular basis
Troubleshooting
- Record and report false-positives promptly
- Temporarily disable a specific rule for testing
- Utilize custom whitelists when necessary
Notes
- Certain rules may affect normal access to some sites
- We recommend checking for rule updates regularly
- If frequent false-positives occur, please contact us immediately
For users who need more flexible control, we offer a Pro service that supports fully custom rule configuration. Should you have any questions, feel free to reach out.
Need help?
Contact on WeChat
private6688
or
Send email
service1@nullprivate.com
Please describe your issue in detail, and we will respond as soon as possible.
Trial Service Details
As a provider focused on delivering custom ad-filtering rules, we understand the considerations users have when choosing a service. Although our operating costs are high, we remain committed to giving users maximum customization flexibility.
To let you fully appreciate the value of our service, we’ve launched an exceptional trial plan. This version includes all premium features and is identical to the paid service, allowing you to experience the unique advantages of customized filtering with zero risk.
Trial notes:
- The discounted price is available only for first-time use
- Renewals require selecting a paid service plan
- Thanks to our account-free design, the trial can be purchased repeatedly
- Each new purchase creates a completely fresh service instance
- Renewals preserve all existing configurations of the original instance
We look forward to your experiencing this premium service. If you encounter any issues during use, our support team is ready to provide professional assistance at any time.
Need help?
Contact on WeChat
private6688
or
Send email
service1@nullprivate.com
Please describe your issue in detail, and we will respond as soon as possible.