This is the multi-page printable view of this section. Click here to print.
Cyber Subtlety
1 - How to Prevent Personal Information Leaks and "Doxxing" Risks
Beware of Risks from Piecing Together Scattered Information
In the Internet age, personal information exists in fragmented form across various platforms and services. Many people believe that leaking small pieces of information is harmless. However, the online environment is not absolutely secure, and malicious actors can collect and combine these scattered bits to reconstruct a complete personal profile. Even a simple search engine can be used for data gathering.
Take a certain social platform as an example: while users share snippets of their lives, they may inadvertently expose personal details. Some users like to publicly discuss the meaning and usage scenarios of their passwords, which undoubtedly increases the risk of those passwords being cracked.
Social-engineering principles tell us that meaningful strings often appear repeatedly in multiple places. A unique username or an easy-to-remember password is likely reused across different platforms, making it a common vector for information leaks.
Reduce Account Linkage to Protect Your Identity
For ordinary netizens who have no need to build a personal brand, it is recommended to use randomly generated usernames and passwords to minimize the correlation between accounts on different platforms.
Note that merely using different credentials is not enough to eliminate account linkage. If identical or similar content is posted under accounts on different platforms, they can still be identified as belonging to the same person.
Common Types of Sensitive Information
Below are some common types of sensitive information that require extra care:
- Passwords
- Usernames
- Avatars
- Birthdays
- Addresses
- Phone numbers
- Email addresses
- QQ numbers
- WeChat IDs
- Personal websites
- Geolocation data
- Photos
Malicious actors often integrate leaked personal information from various sources using “social-engineering databases.” For instance, if two separate platform leaks contain the same phone number, it is highly probable that both records belong to the same individual.
Even if usernames and photo styles differ across platforms, they can still be linked via these databases to compile a comprehensive personal dossier.
This is not fear-mongering; it is a common application of social-engineering databases. The barrier to using such databases for information gathering and doxxing is low—even minors can master them easily.
Raise Cybersecurity Awareness to Safeguard Your Privacy
While the Internet brings people closer, it can also widen the gap between them. Social platforms provide spaces for communication, yet they can also make users feel more isolated.
In the online world, we long to express ourselves and find resonance, but we must also stay vigilant and protect our privacy.
There is no need to reveal every detail of your life to strangers online. Speak cautiously, act prudently, enjoy solitude, and improve yourself—only then can you navigate the digital realm with ease.
Recommendations:
- Regularly review and update your passwords to ensure they are strong.
- Avoid reusing the same username and password across different platforms.
- Be careful when sharing photos or posts that contain personal information.
- Use tools like NullPrivate to protect your DNS queries and prevent DNS leaks.
- Stay informed about the latest cybersecurity trends to understand emerging threats and countermeasures.
2 - Guide to Protecting Personal Online Privacy
Why Protect Online Privacy?
In the digital age, every online action we take can leave traces:
- Browsing history is tracked
- Personal preferences are analyzed
- Location data is collected
- Social relationships are mapped
Basic Protective Measures
1. Browser Configuration
- Use private/incognito mode
- Disable third-party cookies
- Enable “Do Not Track”
- Regularly clear browsing data
2. Search Engine Choices
- Use anonymous search engines (e.g., DuckDuckGo)
- Avoid searching sensitive content while logged in
- Cross-verify with multiple search engines
3. DNS Encryption Protection
- Enable DNS-over-HTTPS
- Use private DNS services
- Avoid default DNS servers
Advanced Protection Strategies
1. Network Access Protection
- Use trusted services
- Enable HTTPS-Only mode
- Avoid public Wi-Fi
2. Ad-Tracking Protection
- Install ad blockers
- Use content filters
- Turn off personalized ad options
3. Social Media Privacy
- Review privacy settings
- Limit sharing of personal information
- Disable location services
- Be cautious with third-party logins
Daily Usage Recommendations
Reduce Your Digital Footprint
- Use temporary email services
- Avoid registering with real names
- Use different passwords on different platforms
- Regularly check authorized applications
Prevent Privacy Leaks
- Use a password manager
- Enable two-factor authentication
- Encrypt important files
- Be careful when installing new apps
Points to Note
- Use privacy-protection tools appropriately
- Comply with local laws and regulations
- Keep software updated promptly
- Cultivate privacy-protection awareness
Complete anonymity is hard to achieve, but the measures above can significantly raise your level of personal privacy protection. Choose the protections that suit you and strike a balance between convenience and security.
3 - Adolescent Online Safety Protection Guide
Challenges in the Online Environment for Today’s Adolescents
In the digital age, adolescents face unprecedented online challenges:
- Vast amounts of information of varying quality
- Limited ability to identify online risks
- Susceptible to harmful content
- Lack of self-management awareness
Intelligent Protection Solutions
1. Application Access Management
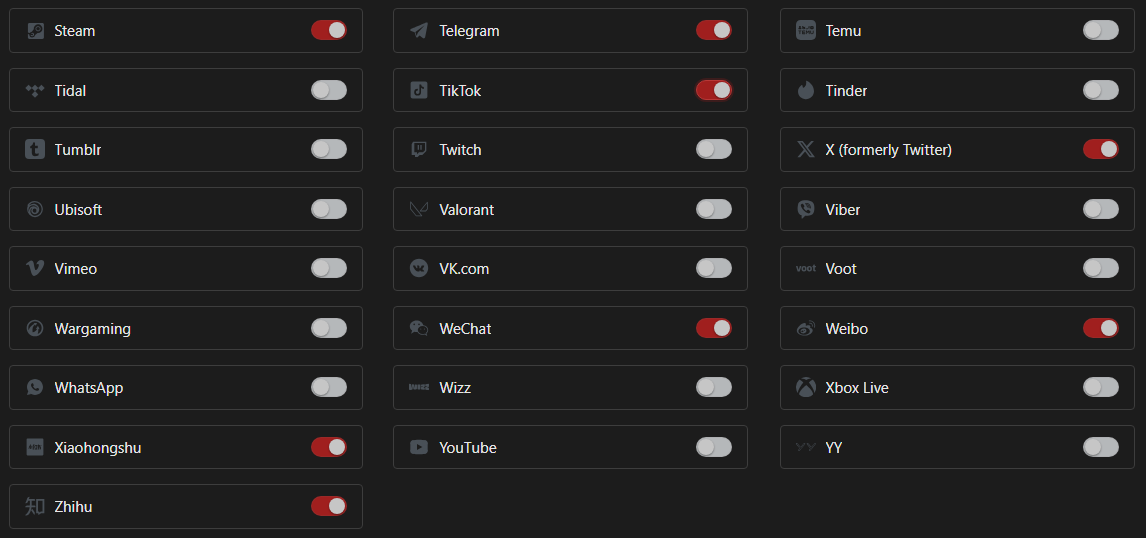
Features:
- Precisely control accessible applications
- Prevent installation of inappropriate software
- Protect personal information security
2. Time Management System
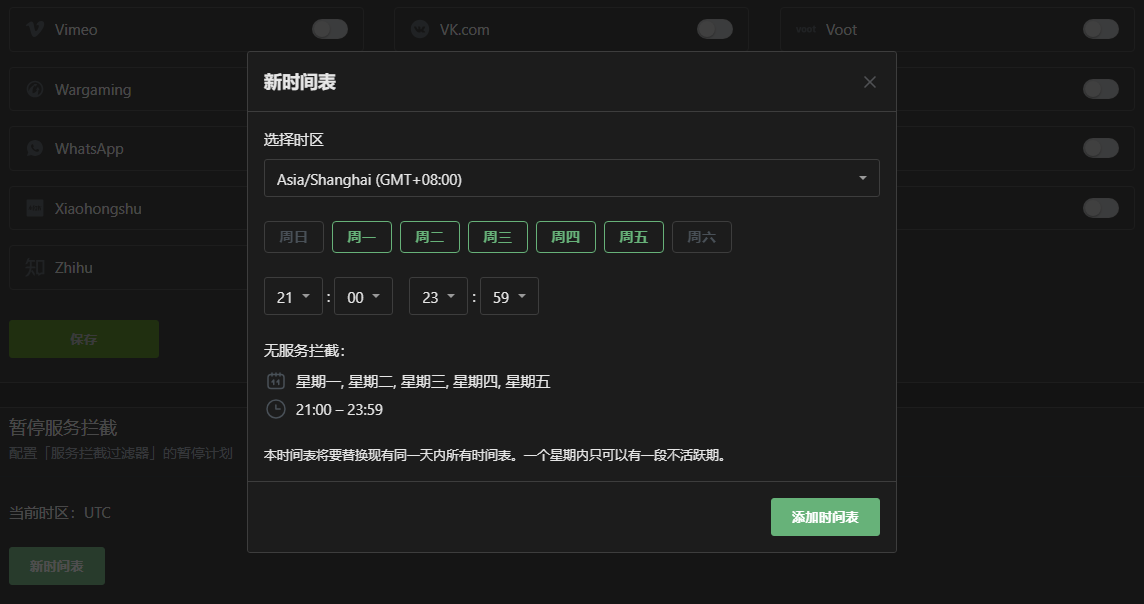
Functions:
- Set reasonable usage time periods
- Prevent internet addiction
- Foster healthy sleep habits
3. Behavior Monitoring and Guidance
Access Log Analysis
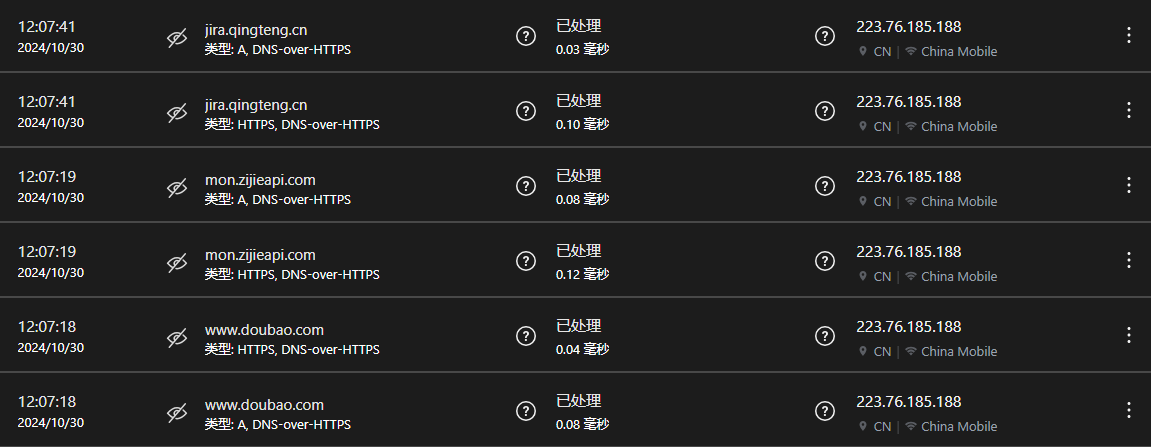
Uses:
- Understand online behavior patterns
- Identify potential risks in a timely manner
- Provide targeted guidance and communication
Intelligent Blocking Settings

Customizable:
- Content rating filtering
- Personalized protection rules
- Dynamic policy adjustment
Parental Guidance Recommendations
Beyond protective measures, good family education is more important:
- Have open conversations with children about internet use
- Cultivate independent thinking and judgment abilities
- Establish a mutual trust communication mechanism
- Gradually relax controls step by step
Technical means are auxiliary tools, while education and guidance are fundamental. Use control tools reasonably while focusing on cultivating adolescents’ online literacy and self-management abilities.
4 - Protecting Seniors from Online Scams
Online Risks Faced by Seniors
In today’s society, seniors are confronting increasingly severe cybersecurity threats. The following characteristics make them a high-risk group for online fraud:
- Limited proficiency in smartphone operation
- Lack of awareness and knowledge about online scams
- Limited exposure to cybersecurity information
- Tendency to trust unverified software download links
Technical Protection Solutions
AdGuard Security Protection
AdGuard offers professional malware-blocking capabilities:
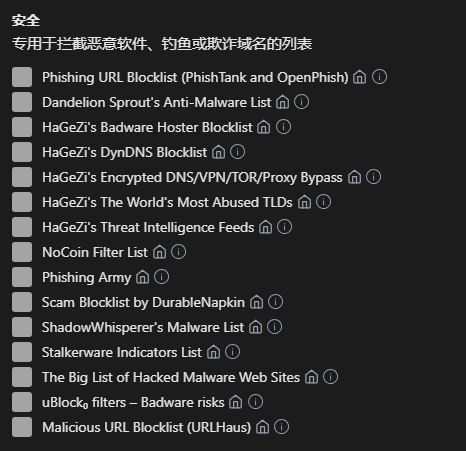
This solution provides the following advantages:
- Runs in the cloud, no additional app installation required
- Zero system resource usage
- Simple configuration and difficult to misconfigure
- Continuous automatic protection
Real-World Results
After a year of implementation, we observed significant improvements:
- Substantial reduction in “phone cleanup” requests
- Enhanced daily user experience
- Decreased smartphone-related frustrations
Comprehensive Protection Strategy
While technical measures are important, all-around protection also requires:
- Regular companionship and communication to understand usage difficulties
- Patiently explaining basic cybersecurity knowledge
- Staying vigilant and identifying potential threats promptly
Technology is a tool, but care is the foundation. Regular companionship and patient guidance are the best ways to protect seniors from online risks.
5 - How to Deal with Enterprise Network Monitoring
Evolution of Enterprise Network Monitoring
Modern enterprises have transitioned from traditional physical monitoring (such as cameras and on-site patrols) to more sophisticated digital surveillance systems. This shift makes monitoring more covert and cost-effective.
Common Network Monitoring Methods
A core method of enterprise network monitoring is tracking via DNS servers. The specific implementations include:
- Deploying dedicated DNS servers within the corporate network
- Enforcing corporate DNS through DHCP services
- Establishing a mapping between IP addresses and workstation locations
Technical Principles of Monitoring
Even with widespread HTTPS adoption, DNS queries are still transmitted in plaintext. This means:
- All domain-resolution requests are logged
- While the specific content accessed cannot be seen, the visited domain names are known
- Combined with timestamps, this allows analysis of employees’ browsing behavior patterns
Personal Privacy-Protection Solutions
To reasonably protect personal privacy, consider the following options:
- Use your personal mobile network
- Configure a private DNS service
- Employ a secure VPN service
Please note: When implementing any privacy-protection measures, comply with relevant laws, regulations, and corporate policies.